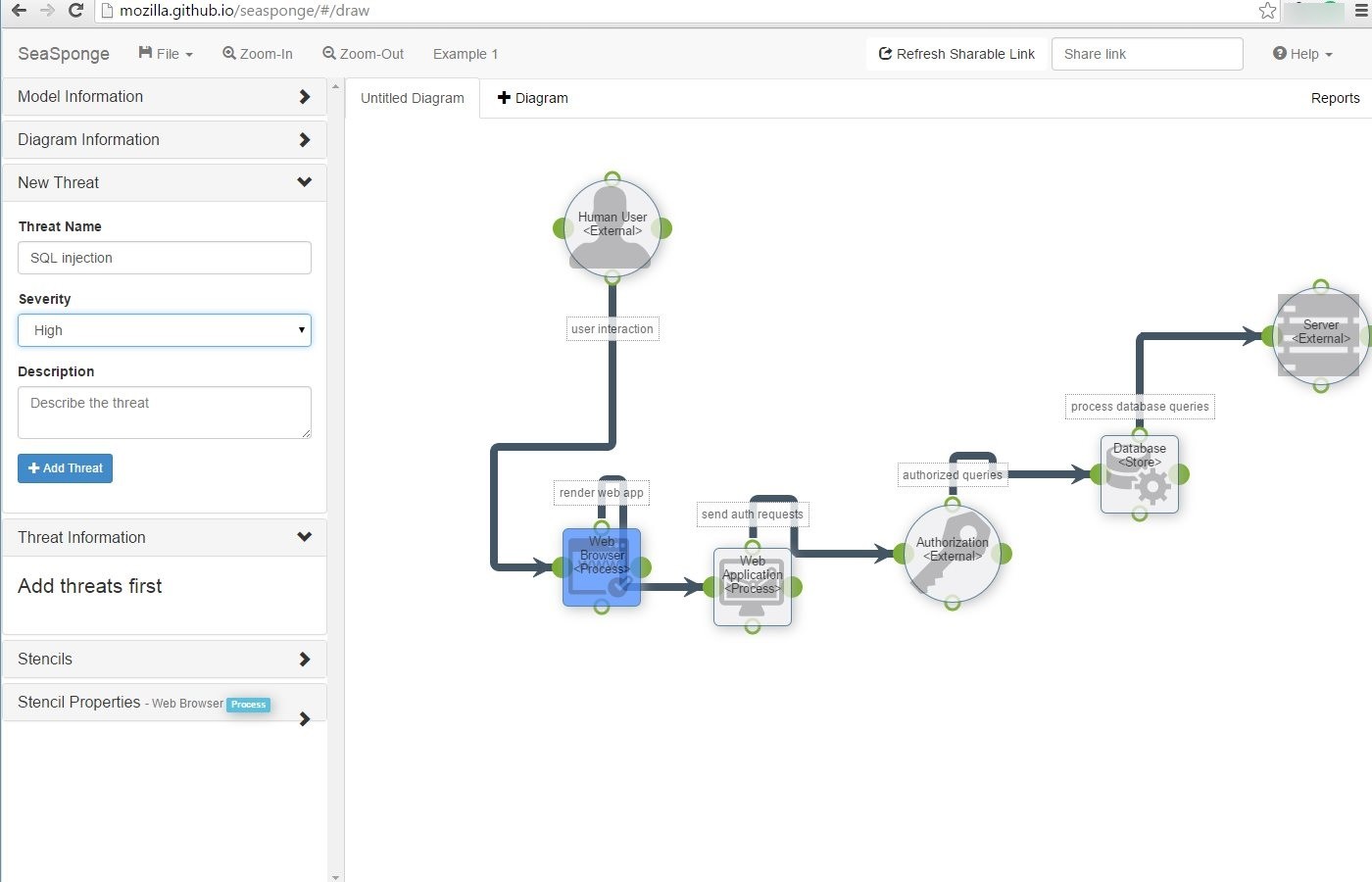
A model validation toggle feature was added to the tool's Options menu. Several links in the threat properties were updated. Minor UX changes were made to the tool's home screen. The Threat Modeling Tool now inherits the TLS settings of the host operating system and is supported in environments that require TLS 1.2 or later. “Microsoft Threat Protection truly is a cloud-based solution that uses a lot of artificial intelligence and machine learning at the endpoint to understand and recognize threats, to be able to. Application Threat Modeling Threat modeling works to identify, communicate, and understand threats and mitigations within the context of protecting something of value.
- Microsoft Threat Modeling Tool For Mac Pro
- Microsoft Threat Modeling Tool Samples
- Microsoft Threat Modeling Tool 2016 Mac
- Microsoft Threat Model Tool Download
Microsoft today shared a bunch of security news ahead of RSAC 2020 that kicks off next week in San Francisco. The biggest announcement is arguably the general availability of Microsoft Threat Protection, which uses AI to offer a correlated view of threats and automation to address them. Other tidbits worth touching on include news from Microsoft Defender ATP (Android and iOS support is coming), Insider Risk Management, and Azure Sentinel.
Microsoft released a public preview of Microsoft Threat Protection in December. At the time, the company described “an integrated solution” built on Microsoft Defender Advanced Threat Protection (ATP) for endpoints, Office 365 ATP for email and collaboration tools, Azure ATP for identity-based threats, and Microsoft Cloud App Security (MCAS) for SaaS applications. In short, Microsoft Threat Protection shares threat insights between these products to help stop the progression of an attack. Until now, these products talked to each other “but not automatically and at scale,” Ann Johnson, corporate vice president at Microsoft, told VentureBeat. The communication lines were already open, but by announcing general availability today, the company is signaling its confidence in “being able to detect the threats, block the threats, and then pass that information along in milliseconds.”
Earlier this year, Microsoft shared that the custom algorithms and machine learning models built into Microsoft Security solutions are trained on 8 trillion daily threat signals. Microsoft Threat Protection uses this AI to help security teams prioritize and act on all the various alerts across their organizations. It proactively hunts for threats across users, email, applications, and endpoints (Windows, macOS, and Linux). The solution investigates threats, responds to them, and automatically restores affected assets to a secured state without any human intervention.
Microsoft Defender ATP for Linux, Android, and iOS
“Microsoft Threat Protection truly is a cloud-based solution that uses a lot of artificial intelligence and machine learning at the endpoint to understand and recognize threats, to be able to detect them, to block them in real time, to block them at global scale, and to communicate across the platforms,” Johnson said. “So if the Windows endpoint sees a threat, it will tell Office. If the Office endpoint sees a threat, it’s going to notify Azure Storage or Azure Server or notify Windows. And now that we’re going to have that cross-platform support, we’ll have that capability also with an extended reach.”
Back in March, Microsoft rebranded Windows Defender as Microsoft Defender to signal it was extending its endpoint protection platform to additional operating systems. The company launched Microsoft Defender Advanced Threat Protection (ATP) for Mac in limited preview then and followed up with a private preview in December.
Microsoft Defender ATP for Windows and macOS offers preventative protection, post-breach detection, and automated investigation and response. Today, the company announced the public preview of preventative protection capabilities for Linux servers. It supports the following Linux server versions: RHEL 7+, CentOS Linux 7+, Ubuntu 16 LTS or higher LTS, SLES 12+, Debian 9+, and Oracle EL 7.
Even more notably, Microsoft today announced plans to bring Microsoft Defender ATP to mobile platforms this year. That means Android and iOS devices will get antivirus protection and a full command line experience. In the Microsoft Defender Security Center, you’ll be able to see basic alerts and machine information. You can’t offer enterprise security without offering protection on mobile as well.
Insider Threat Protection
Microsoft Threat Modeling Tool For Mac Pro
Microsoft today also announced the general availability of Insider Risk Management. As the number of mobile devices grows, so does the amount of corporate data that can be easily transported and accessed anywhere. Insider Risk Management aims to help IT departments identify, remediate, and prevent insider risks. Plus, it doesn’t require deploying agents or configuring data ingestion.
First available as a preview in November, Insider Risk Management extends the same Microsoft Information Protection tech that already classifies and protects more than 50 billion documents for Microsoft customers. The service leverages AI and machine learning to identify anomalies in user behavior and flag high-risk activities. Specifically, the ML algorithms consider variables like file activity, communications sentiment, and abnormal user behaviors. Microsoft promises that the tool identifies patterns and risks in a privacy-preserving fashion (names are anonymized). The offering also includes an IP Theft template and previews of Harassment, Confidentiality, and Security templates.
“Really driven by a lot of customer demand, but also driven by our own internal organization, was the need to do something around insider risk management and actually throw machine learning again at this problem,” Johnson told VentureBeat. “What our customers tell us today, and the research tells us, [is] that over 50% of breaches have some type of insider element.”
Azure Sentinel
When announcing Azure Sentinel, which hit general availability in September, Microsoft called it the first native Security Information and Event Management (SIEM) tool built by a major cloud provider. The cloud-based SIEM uses AI to “reduce the noise” and deliver intelligent security analytics across the enterprise. Azure Sentinel can turn “huge volumes of low fidelity signals” into “a few important incidents for security professionals to focus on.”
In that vein, Microsoft today shared that Azure Sentinel evaluated nearly 50 billion suspicious signals within the company in December 2019 to emit 25 high-confidence incidents for investigation. Of course, 50 billion signals would be impossible for employees to manually analyze in a month, even for a company of Microsoft’s size.
Microsoft Threat Modeling Tool Samples
On February 24, Azure Sentinel is getting the following enhancements:
- New built-in connectors: Data connectors and workbooks from partners like Forcepoint, Zimperium, Quest, CyberArk, and Squadra. The new connector for Azure Security Center for IoT makes Azure Sentinel the first SIEM with native IoT support.
- New resources: Developer docs, guides, samples, validation criteria, and updated GitHub Wiki.
- Import AWS CloudTrail logs for no additional cost until June 30: Azure Sentinel provides security insights across the entire enterprise, not just on Microsoft workloads.
Microsoft Threat Modeling Tool 2016 Mac
That last point is one that Microsoft really wants to drive home. You can already ingest Microsoft Azure activity logs, Office 365 audit logs, and Microsoft 365 security alerts for free with Azure Sentinel. But Amazon Web Services is bigger than Microsoft Azure, so this promotion is meant to woo those customers.
Microsoft Threat Model Tool Download

“We also want to make certain that our customers know that even though the solution is called Microsoft Azure Sentinel, it is actually a solution that was fully built and contemplated to be like any other SIEM in the market — being cross-cloud and being able to work in any environment in a very heterogeneous way,” Johnson said. “We really want our customers to be able to test that heterogeneous environment for themselves in a very low-risk manner.”